It was not so long ago that all resources and users were inside the network perimeter. Network security, and an antivirus on endpoints, were pretty much everything we needed.
However, the Internet has changed the way we do business today.
➤Employees, partners, and subcontractors, some of whom use their own devices, are now among our users.
➤We work remotely, using our business laptop or our own workstation to access corporate resources as well as those of our customers and suppliers.
➤We save sensitive information in the cloud.
➤We deploy devices connected to our supply chains, our fields, our factories and our buildings.
The old security model is no longer capable of meeting the new data protection standards.
Consider the following scenario:
🔹When fraudsters get access to a perimeter's endpoints, they can travel laterally to extract critical information.
🔹Phishing attacks and identity theft allow attackers to steal users' identities and get access to their data.
We now live in a different world, and we can no longer think that everything that occurs behind the corporate firewall is secure.
Zero Trust
The Zero Trust paradigm comes into play here.
All IT industry companies, including Microsoft, the NIST, Google, and Fortinet, have adopted this method.
Why should you use this model right now?
Zero Trust is a must-have adjustment in the security strategy to appropriately address big changes in:
Assets must be safeguarded.
Attack strategies have evolved throughout time.
Cyber-attacks, such as ransomware, have disastrous repercussions.
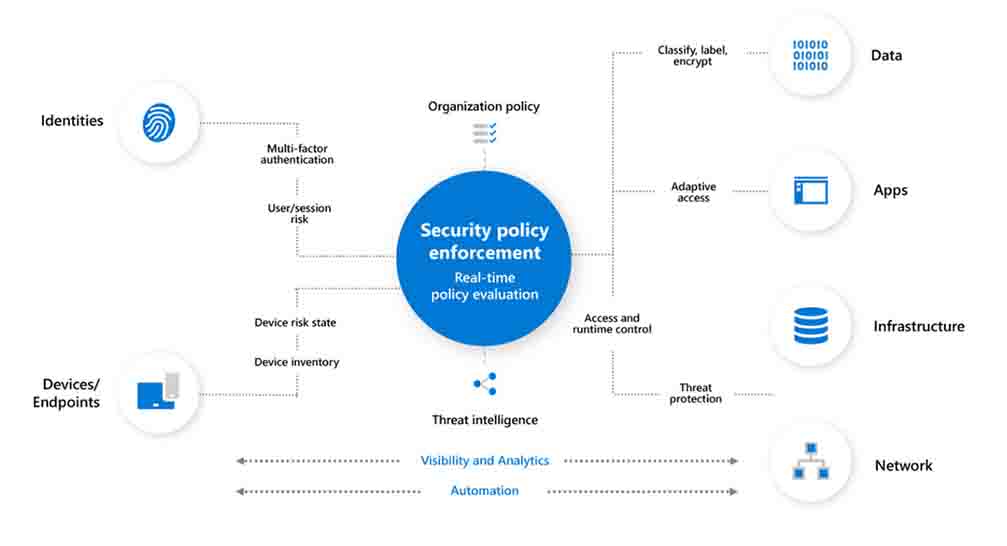
What does it involve?
The Zero Trust concept includes the following three principles:
🔸Regardless of location, all resources must be available in a secure manner from a secure machine.
🔸 Access control is based on the "need to know" associated with a person's identity and the resources that this user has access to.
🔸 A zero-trust security approach implies that every network has been hacked, every machine has been compromised, and every user is at danger. As a result, information must be saved and analyzed for verification reasons.
What is the plan of action?
Zero Trust is a model, a way of thinking, and a strategy. As a result, the roadmap is unique to your business.
You should try to achieve the following goals in stages:
🟩 Reduce your vulnerability to the following attack surfaces:
🟩 Authentication: Improve identification (multi-factor authentication, conditional access)
🟩 Devices: Implement advanced detection and response protection, control applications with fine tuning, and improve device administration.
🟩 Applications: Ensure adequate application rights, access control, and aberrant behavior monitoring.
🟩 Networks: Use network segmentation and lateral movement restrictions to keep illegal resources out.
🟩 Data: Ensure that data is accessible and that data flows are secure.
🟩 Using a S.I.E.M. system, we can improve our security operations.
Of course, you should always begin by conducting audits to discover your vulnerabilities, then analyze them and prioritize your action plan and procedures based on your risk tolerance.
However, it is self-evident that securing identities and devices is of paramount importance, since these two surfaces are now the most targeted and pose your greatest threats.
Cybercriminals are currently exploiting the weaknesses in your systems to take advantage of your out-of-date defense.
So that's where you should start, because these two measures will give you with the most value for the least amount of money.
Emergency measures
These two measures should be implemented right now.
🟨Multi-factor authentication should be implemented for Internet-connected systems including e-mail, remote desktop, and VPN.
🟨With a behavior-based advanced threat and protection detection system, you can keep your endpoints safe.
After you've fixed these two flaws, you'll have more time to create a more detailed roadmap.








