

Instead of believing everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an uncontrolled network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” In a Zero Trust model, every access request is strongly authenticated, authorized within policy constraints and inspected for anomalies before granting access. Everything from the user’s identity to the application’s hosting environment is used to prevent breach. We apply micro segmentation and least privileged access principles to minimize lateral movement. Finally, rich intelligence and analytics helps us identify what happened, what was compromised, and how to prevent it from happening again.
Guiding principles of Zero Trust:
1. Verify explicitly.
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
2. Use least privileged access.
Limit user access with Just In Time and Just Enough Access (JIT/JEA), risk based adaptive polices, and data protection to protect both data and productivity.
3. Assume breach.
Minimize blast radius for breaches and prevent lateral movement by segmenting access by network, user, devices, and application awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.

Building Zero Trust into your organization
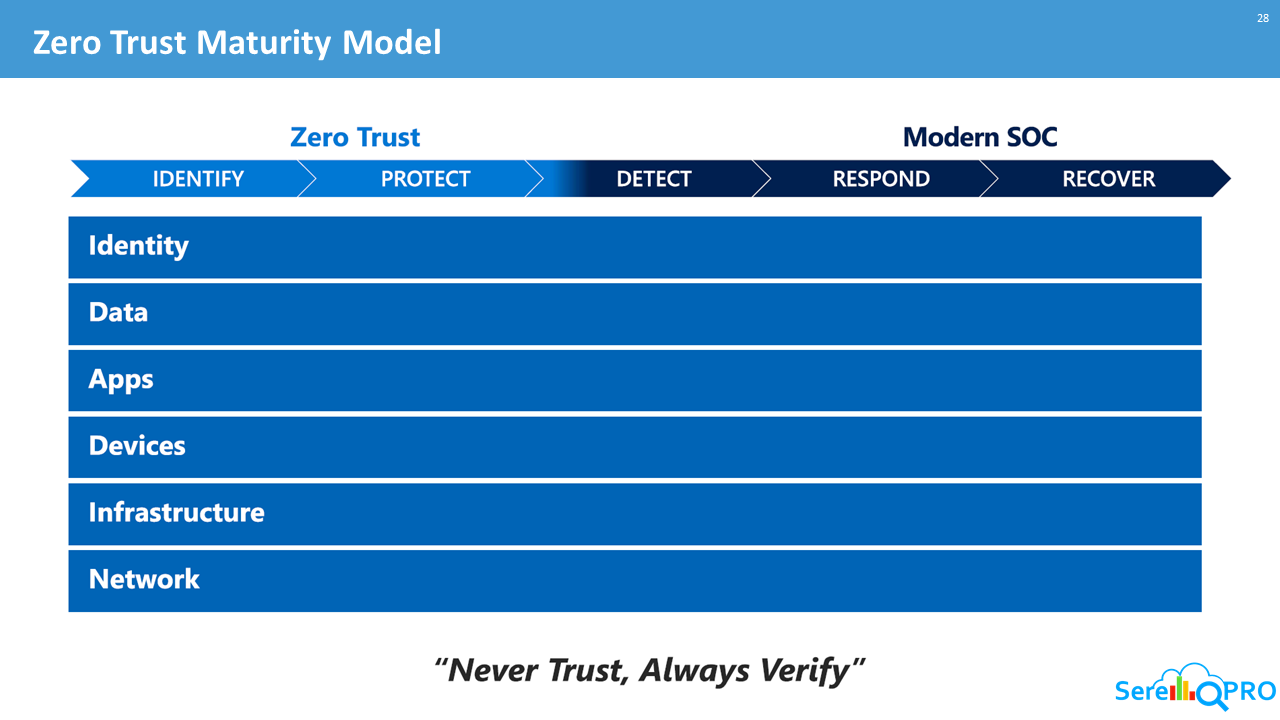
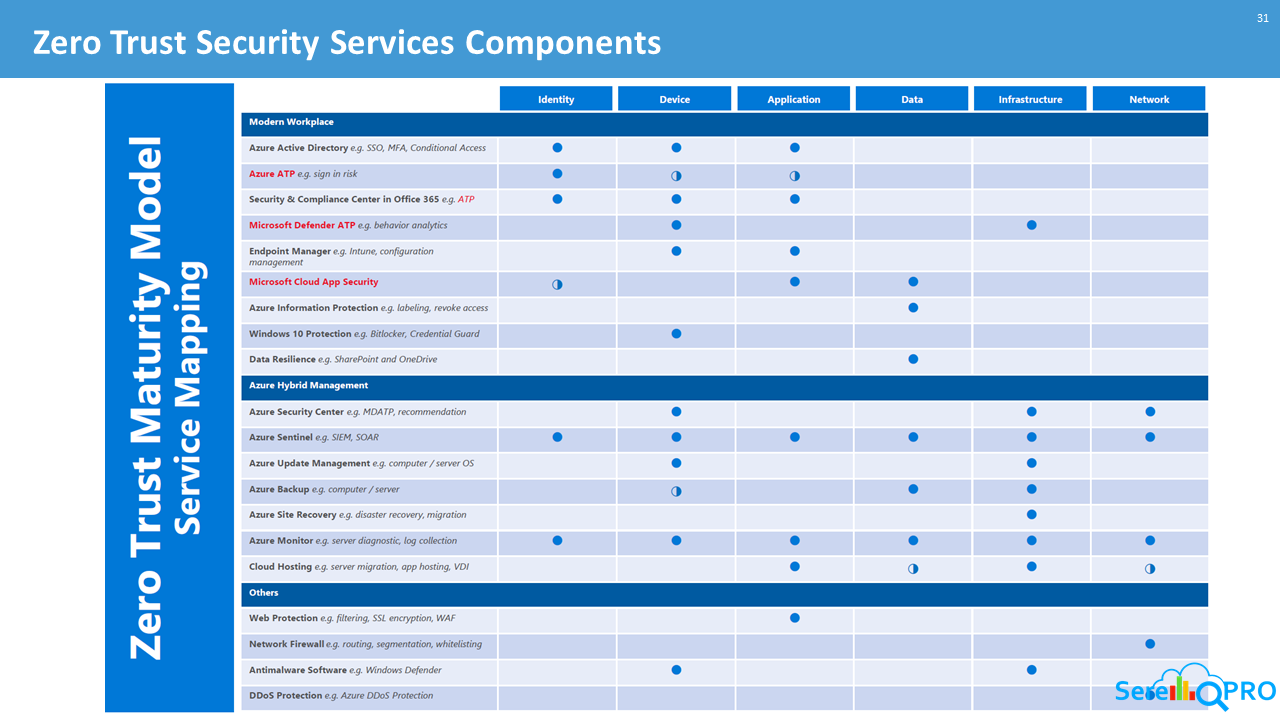
A Zero Trust approach should extend throughout the entire digital estate and serve as an integrated security philosophy and end to end strategy. This is done by implementing Zero Trust controls and technologies across six foundational elements: identities, devices, applications, data, infrastructure, and networks. Each of these six foundational elements is a source of signal, a control plane for enforcement, and a critical resource to be defended. This makes each an important area to focus investments.
- Identities
Identities whether they represent people, services, or IOT devices define the Zero Trust control plane. When an identity attempts to access a resource, we need to verify that identity with strong authentication, ensure access is compliant and typical for that identity, and follows least privilege access principles.
- Devices
Once an identity has been granted access to a resource, data can flow to a variety of different devices from IoT devices to smartphones, BYOD to partner managed devices, and on premises workloads to cloud hosted servers. This diversity creates a massive attack surface area, requiring we monitor and enforce device health and compliance for secure access.
- Applications
Applications and APIs provide the interface by which data is consumed. They may be legacy on premises, lift and shifted to cloud workloads, or modern SaaS applications. Controls and technologies should be applied to discover Shadow IT, ensure appropriate in app permissions, gate access based on real time analytics, monitor for abnormal behavior, control of user actions, and validate secure configuration options.
- Data
Ultimately, security teams are focused on protecting data. Where possible, data should remain safe even if it leaves the devices, apps, infrastructure, and networks the organization controls. Data should be classified, labeled, and encrypted, and access restricted based on those attributes.
- Infrastructure
Infrastructure (whether on premises servers, cloud based VMs, containers, or micro services) represents a critical threat vector. Assess for version, configuration, and JIT access to harden defense, use telemetry to detect attacks and anomalies, and automatically block and flag risky behavior and take protective actions.
- Networks
All data is ultimately accessed over network infrastructure. Networking controls can provide critical “in pipe” controls to enhance visibility and help prevent attackers from moving laterally across the network. Networks should be segmented (including deeper in network micro segmentation) and real time threat protection, end to end encryption, monitoring, and analytics should be employed.
Zero Trust across the digital estate
In an optimal Zero Trust implementation, your digital estate is connected and able to provide the signal needed to make informed access decisions using automated policy enforcement. Let’s explore how the major components of the Zero Trust model all work together to deliver end-toend coverage.
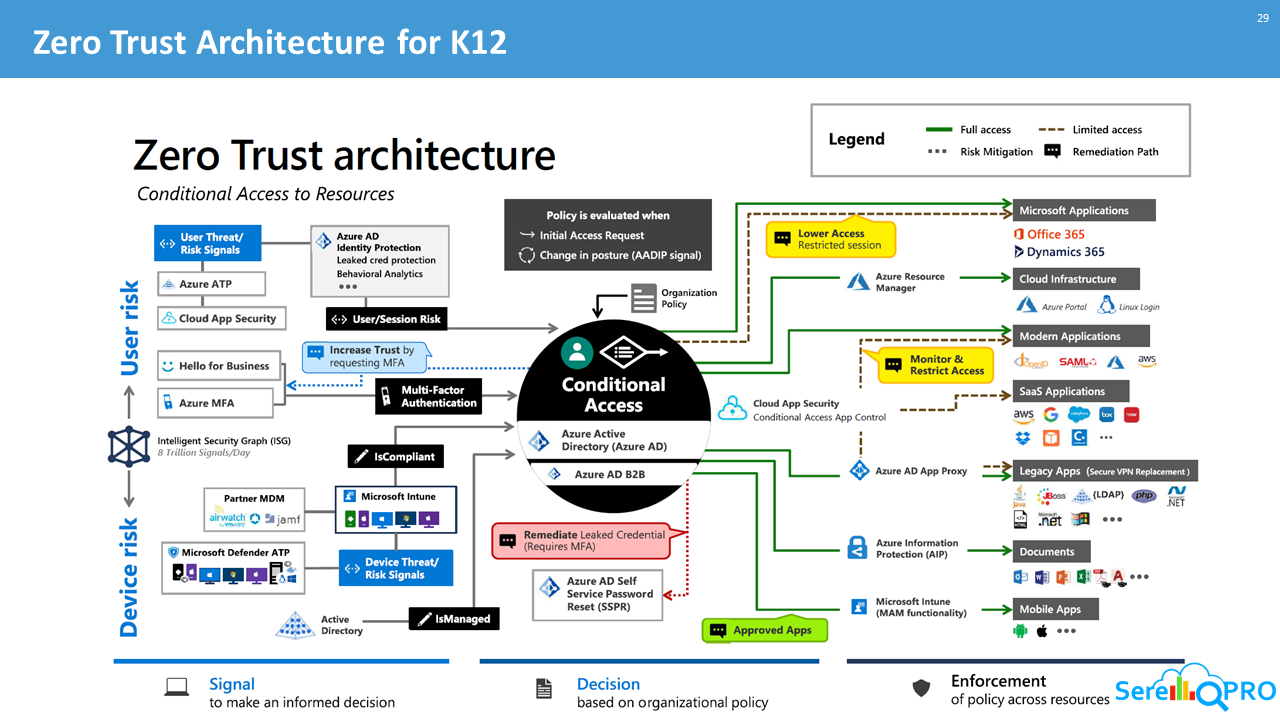
Tools to drive your Zero Trust implementation
As you begin to assess your Zero Trust readiness and begin to plan on the changes to improve protection
across identities, devices, applications, data, infrastructure, and networks, consider these key
investments to help drive your Zero Trust implementation more effectively. Through our own experience,
we’ve found each of the following to be critical to closing important capability and resources gaps:
1. Strong authentication.
Ensure strong multi factor authentication and session risk detection as the backbone of your access strategy to minimize the risk of identity compromise.
2. Policy based adaptive access.
Define acceptable access policies for your resources and enforce them with a consistent security policy engine that provides both governance and insight into variances.
3. Micro segmentation.
Move beyond simple centralized network based perimeter to comprehensive and distributed segmentation using software defined micro perimeters.
4. Automation.
Invest in automated alerting and remediation to reduce your mean time to respond (MTTR) to attacks.
5. Intelligence and AI.
Utilize cloud intelligence and all available signals to detect and respond to access anomalies in real time.
6. Data classification and protection.
Discover, classify, protect, and monitor sensitive data to minimize exposure from malicious or accidental exfiltration.
In closing
While a Zero Trust security model is most effective when integrated across the entire digital estate, most organizations will need to take a phased approach that targets specific areas for change based on their Zero Trust maturity, available resources, and priorities. It will be important to consider each investment carefully and align them with current business needs. The first step of your journey does not have to be a large lift and shift to cloud based security tools. Many organizations will benefit greatly from utilizing hybrid infrastructure that helps you use your existing investments and begin to realize the value of Zero Trust initiatives more quickly.
Fortunately, each step forward will make a difference in reducing risk and returning trust in the entirety of your digital estate.

